IBM CCA API
CCA stands for the Common Cryptographic Architecture API as implemented on the hardware security module IBM 4758, which is an IBM cryptographic coprocessor widely used in security critical systems such as electronic payment and automated teller machine (ATM) networks.
The CCA API contains several protocols, namely the CCA-0 protocol, which is subject to an attack presented by Bond, and other versions of this protocol (CCA-1A, CCA-1B, CCA-2B, CCA-2C, and CCA-2E), designed to avoid this attack.
The CCA is a key management system, which provides commands that use encrypted keys to achieve desired functions. A 168-bit triple-DES key, known as the master key, is stored in the security module’s tamper proof memory and is used to encrypt all other keys which are then kept on the host computer. These other keys, known as working keys, are used to perform the various functions provided by the CCA API. There are several types of working keys, depending on the type of action they will be involved. The CCA API supports the following functions and features:
-
– Encryption and decryption of data, using the DES algorithm.
-
– Message authentication code (MAC) generation, and data hashing functions.
-
– Generation and validation of digital signatures.
-
– Generation, encryption, translation and verification of Personal Identification Number (PIN) and transaction validation messages.
-
– General key management facilities.
-
– Administrative services for controlling the initialization and operation of the security module.
As some of the provided commands are particularly sensitive, the CCA en- forces an access-control system, whereby certain commands are only available under specific circumstances. It is, however, the responsibility of the device administrator to ensure that the correct separation of duty provided is upheld.
The CCA API uses four main types for classifying DES working keys, each of which is further sub-divided into more specific and restrictive types. A working key is stored outside of the security module, encrypted under the exclusive-or of the device’s master key and the control vector representing the type of the key. The main key types, and their uses, are as follows:
-
– Data Keys: keys of this type are used to encipher and decipher arbitrary data, as well as for the generation and verification of message authentication codes (MACs).
-
– PIN Keys: this type covers keys which are used for PIN block encryption, PIN block decryption, PIN generation and verification, and just PIN verification.
-
– Key Encryption Keys (KEK): these keys are used to encrypt and decrypt other working keys during transfer between security modules, and are divided into import and export types. Keys encrypted under an export key are referred to as external keys, as they must be imported into a security module before they can be used.
-
– Key Generation Keys: the CCA API provides commands which generate DES keys given an initial key, and will typically use the provided key to encrypt or decrypt a supplied piece of data.
The typing mechanism restricts the working keys that can be used for a particular command. For example, the PIN derivation key (PDK) used in the verification of a customer’s PIN, cannot be used to encrypt arbitrary data.
The following constants and variables are used throughout this section to denote the various control vectors, cryptographic keys and other exchanged data.
-
– constant DATA: control vector for data keys
- – constant IMP: control vector for import-type key encryption keys
-
– constant EXP: control vector for export-type key encryption keys
-
– constant KP: a part of a key, and not a complete key
-
– constant KM: the security module’s master key
-
– constants Km1, Km2, and Km3. These are used as a simplification of the CCA protocol where it is assumed that the environment produces the term e(IMP * KP * KM, Km1 * Km2).
-
– variable ekek: an arbitrary key encryption key
-
– variable eK : a key generation key to encrypt messages
-
– variable T: an unknown, randomly generated, new cryptographic key or an arbitrary key type control vector. This variable is restricted to constants DATA, IMP, EXP and PIN.
-
– variables km1, km2, km3: i’th key part (used to build an arbitrary key)
-
– variable X : arbitrary (plain) data
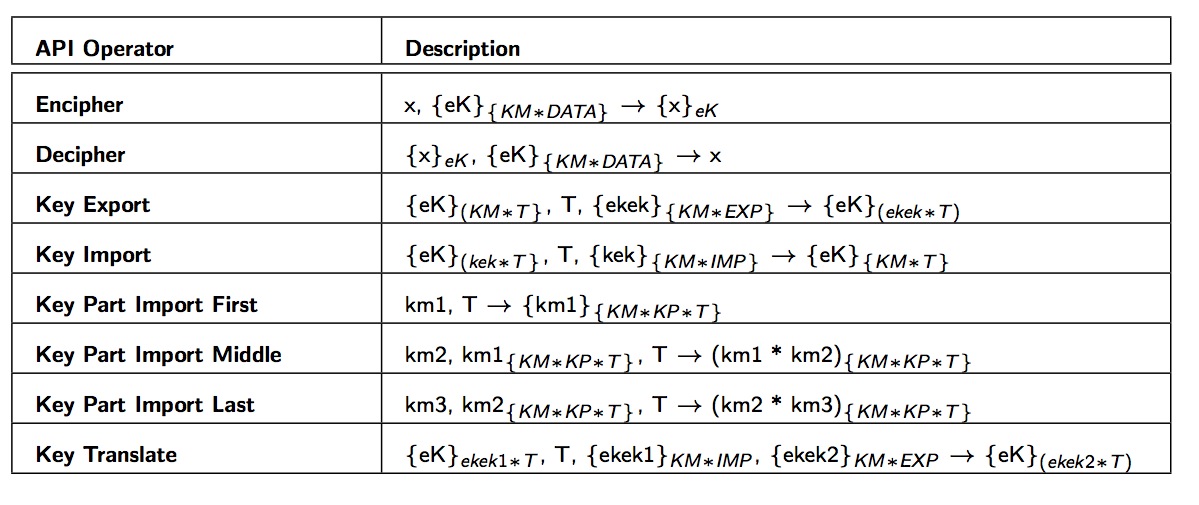
In the following, we provide an informal description of the CCA API’s commands. In the following table we summarize the exchange of messages performed for each com- mand: messages in the left hand side of the “rule” denote the messages that need to be received; whereas the message in the right hand side denotes the message that is sent.
-
Decipher decrypts ciphertext which has been encrypted under the supplied data key eK. The data key can either be of the general type, or one of the subtypes that permits data deciphering.
:: nil :: [(e(eK, X))-, (e(KM ∗ DAT A, eK))-, (X)+]
-
Key Export converts a working key eK from being encrypted under the local master key, to being encrypted under the supplied export-type key encryption key ekek. Note that key ekek must be able to be exported.
:: nil :: [(e(KM ∗ T, eK))-, (T ))-, (e(KM ∗ EXP, ekek))-, (e(ekek ∗ T, eK))+]
-
Key Import converts a key eK from encryption under the supplied import- type key encryption key kek to encryption under the local master key KM. Although not explicitly mentioned in the manual, the key being imported must be a complete key (i.e. it cannot be a key part).
:: nil :: [(e(kek ∗ T,eK))-,(T))-,(e(KM ∗ IMP,kek))-,(e(KM ∗ T,eK))+]
-
The three Key Part Import commands can then be used one after the other, by three different security officers, each in possession of one key part, to create the working import key. In the attack found by Bond [2] these commands were used to change the type of a key, as explained in Section 3.2. Note that km1, km2 and km3 are variables.
:: nil :: [(km1)−, (T ))-, (e(KM ∗ KP ∗ T, km1))+]
:: nil :: [(km2)−, (T ))-, (e(KM ∗ KP ∗ T, km1))-, (e(KM ∗ KP ∗ T, km1 ∗ km2))+]
:: nil :: [(km3)−, (T ))-, (e(KM ∗ KP ∗ T, km2))-, (e(KM ∗ T, km2 ∗ km3))+] -
Key Translate translates a key eK from encryption under one key encryption key to encryption under another. The first key encryption key ekek1 must be of import type (IMP), and the latter must be of export type (EXP).
:: nil :: [((e(ekek ∗ T,eK)))-,(T))-,(e(KM ∗ IMP,ekek1))-, (e(KM ∗ EXP, ekek2))))-, (e(ekek2 ∗ T, eK))+]
Now we explain in more detail the different API commands and provide their strand specification in Maude-NPA.
Encipher encrypts the given plaintext with the supplied data key. The data key can either be of the general Key type, or one of the subtypes that permits data ciphering.
:: nil :: [(X)-, (e(KM ∗ DAT A, eK))-, (e(eK, X))+]
The exact steps that the security module performs for each command have not been included, since the process is virtually the same in all cases. The master key and all control vectors are known to the security module, and any additional information required is either passed on as a plaintext parameter, or is encrypted under a known key. For example, in the case of the Key Import command, the security module knows both KM and IMP and is therefore able to obtain eKek from the third parameter. This key encryption key is then XOR-ed with T, and used to obtain a key eK from the first parameter. Finally, key eK is encrypted under the exclusive-or of KM and T to produce the message {eK}{KM∗T} that is returned by the command.